Tracking Cookies
Tracking cookies are a specific type of cookie that is used to identify users and possibly prepare customized web pages for them. When you enter a web site using cookies, you may be asked to fill in some information for example search criteria. This information is stored on your computer as a cookie file (a small text file). The next time you go to the same web site, or a website that can access the tracking cookies, your browser will send the cookie to the web server. The server can use this information to present you with custom web pages.
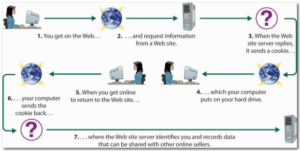
Tracking cookies are not harmful and don’t pose a security risk like malware, worms, or viruses, but they can be a privacy concern as they store and pass information to other websites about websites you have been visiting and information you have been entering into them.
Denial of Service (DoS) Attack
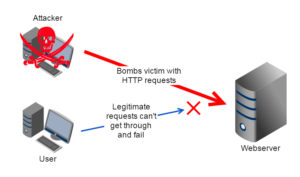
A denial of service (DoS) attack is a cyber attack that involves flooding a web server with a large number of requests so the webpages stored on it become unavailable to legitimate users.
As can be seen from the diagram opposite, this type of DoS attack can be halted quite easily by blocking the attacker using a firewall.
To get round this, attackers are now using DDoS (Distributed Denial Of Service) attacks
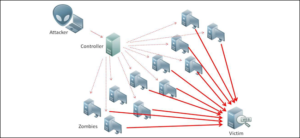
This is where a large number of slave computers (who may not even know they have this spyware installed on them) all send requests for information from the ‘target server’. Because the requests are coming from thousands if not millions of computers, it is much more difficult to clock these attacks.
Types of Attacks
Bandwidth consumption
A smurf attack relies on misconfigured network devices that allow packets to be sent to all computer hosts on a particular network via the broadcast address of the network, rather than a specific machine. The attacker will send large numbers of IP packets with the source address faked to appear to be the address of the victim. The network’s bandwidth is quickly used up, preventing legitimate packets from getting through to their destination.
Resource starvation
The resources that are being starved are items like the computer’s memory, hard disc space and even CPU processing time. For example, a disk space attack, is one in which an attacker is able to consume a particular resource until it is exhausted. For example, an attacker might continuously issue requests to your Web site to create folders or create users. If this occurs, you will eventually run out of disc capacity.
Another example is a memory starvation attack is designed to force your Web site to consume excess memory. If an e-commerce site is the target, then an attacker can continuously add items to ‘baskets’ using a script that adds millions of line items so an attacker will eventually exhaust the available memory of the server, resulting in a DoS.
Domain Name Service (DNS)
A DNS server is a computer server that contains a database of public IP addresses and their associated hostnames, and translates those common names to IP addresses as requested.
For example, to connect to the website www.lifewire.com the computer really needs to know its IP address 151.101.129.121. When you type in the web address in a browser the DNS server translates this into the IP address.
A DoS attack can target the DNS server for a particular company meaning genuine clients when they enter the web address are unable to get it translated to the IP address and are therefore unable to access the website.
DoS Implications
Symptoms
Slow performance
Due to the server being flooded with requests for information the server will be spending so much of its time servicing these requests that other requests e.g. access to a webpage or opening a piece of software will be extremely slow.
Inability to access
At the extreme end, if the server is unable to cope with all these requests then it may crash or shut itself down. Both of these will mean that legitimate users will be unable to access the server.
Effects
Disruption to users and business
A report in 2014 surveyed a large number of companies about DoS attacks and the affect it had on their businesses. 39% of companies said that their server had been down for 1 hour or less. 16% selected between 1 and 4 hours and 6% experienced between 4-8 hours.
Obviously if the main server is not available for this length of time there is severe disruption not only to customers who are maybe trying to access the company website, but also to company employees who are trying to get on with their work.
Cost
Lost revenue
The latest Neustar report on DoS attacks found that the average revenue loss of a DoS attack was about $250,000 per hour.
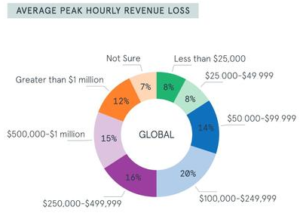
This could either be from customers not being able to buy goods from your website, or from employees not being able to carry out the organisation’s business e.g. trading in stocks and shares.
Labour in rectifying fault
When a DoS attack is detected there is a responsibility on the business to put sufficient security precautions in place to ensure that it doesn’t happen again. This can involve hiring security consultants, designing a new network architecture and buying new hardware and software; this can cost hundreds of thousands of pounds and upwards depending upon the size of the business.
Also when a DoS attack occurs, there is also the worry that other malware may have been planted on the servers that will pass private information to the attackers. A huge amount of time will be spent checking the servers to ensure no malware has been planted.
Reasons
Financial
Criminal gangs use DoS attacks on companies and then tell them they will only stop the attacks if they pay them a certain amount. Because these attacks are slowing down or crashing their servers, some businesses choose to pay this ‘ransom’.
Political
DoS attacks are sometime used for political purposes. Examples are:
- When Russia fell out with Estonia and Georgia a significant increase in the DoS attacks on those countries could be directly attributed to Russia.
- When America imposed increased sanctions on North Korea, a large number of DoS attacks occurred on American companies that were traced back to North Korea.
- In the lead up to the Russian elections in late 2007, the website for the dissident politician and well-known chess Grand Master Gary Kasparov and his political party were both hit with substantial DDoS attacks. Kasparov has been a very vocal counterpoint to the powers in Moscow, specifically former Russian president Putin’s administration, for many years. During the attacks, Kasparov’s site was inaccessible, and so was his political party’s.
- Most recently, in January 2016, the New World Hacking group claimed responsibility for taking down Donald Trump‘s website as they disapproved of some of his politics.
- It is anticipated that the next major war between countries will involve ‘cyber-war’ where DoS and other types of attack will be involved to try and ruin the countries infrastructure.
Personal
Sometimes DoS attacks take place for personal reasons:
- Revenge, when an employee is made redundant they sometimes wish to take revenge on their employer and hence either carry out a DoS attack or pay for one to be carried out.
In hacking circles there is sometimes a level of ‘Kudos’ for bringing down a large server. These are sometimes known as ‘Script Kiddies’ due to the childish motivation of the attacker.
