Encryption
With so much information being transmitted electronically, it is essential that the information be transferred safely and securely. One of the methods of doing this is to use encryption.
Public & Private Key Encryption (Asymmetric Encryption)
Public & Private key encryption (sometimes called asymmetric encryption) involves generating two keys, a public key and a private key. Both keys are mathematically linked using very large prime numbers. Both keys work as a pair.
- Public Key
The public key can be distributed to anyone who wishes to send you a message and they use this public key to encrypt the data. The public key can also decrypt data that has been encrypted with the private key. - Private Key
The private key is known only by you only this private key can be used to decrypt data created by the corresponding public key.
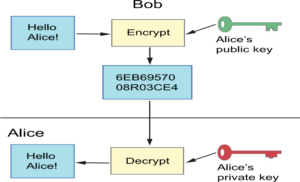
In the example above, Bob wishes to send Alice an encrypted message. Alice sends Bob her public key which he uses to encrypt the message. He then sends the encrypted message to Alice who uses her private key to decrypt the message.
If Alice wished to reply, then she could encrypt the message with her private key and send it to Bob who can decrypt it with her public key.
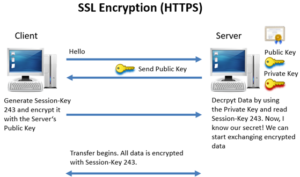
Secure Socket Layer (SSL) is a popular encryption system for secure websites. It operates by:
- Your browser will be sent the website’s public key – the private key remains on the website’s server, so is still secure and cannot be intercepted.
- Your browser, uses the public key to encrypt the data you are sending (for example your credit card details)
- The data is sent back to the server – even if someone has intercepted the public key and your message they still cannot decrypt the message as they do not have the private key.
- Once back at the server, the private key is used to decrypt the message.
Digital Signature
The purpose of a digital signature is to authenticate the identity of the sender and ensure that the content has not been modified en route.
Digital signature are very difficult to forge and can automatically include a date and time. Digital signatures can be used as legal evidence that the message came from the person sending it and it has not been modified.
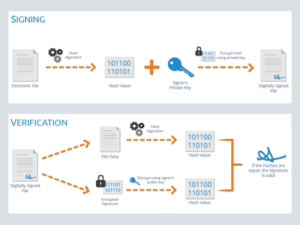
A digital signature is created by:
- A mathematical value (called the hash total) is calculated from the unencrypted data. Because the hash total is calculated from the original message even the slightest change to the message would produce a different hash total.
- The sender of the message encrypts the hash total using their private key and this encrypted total becomes the digital signature.
- The digital signature is added to the message and the entire message (message + digital signature) is encrypted using the recipient’s public key then sent to the recipient.
- The recipient decrypts the message using their private key and decrypts the digital signature using the sender’s public key.
The hash total is then recalculated on the message and if it is the same as the total in the digital signature then the recipient can be sure that the message is from the identified sender and has not been modified in any way during transmission.
Digital Certificate
Hoax digital signatures can be created using a fake private key claiming to be that of a trusted individual. To get around this, a digital certificate verifies that a sender’s public key is formally registered to that particular sender.
Digital certificates are issued by certificate authorities such as Verisign or Symantec. This certificate allows the holder to use the Public Key Infrastructure (PKI).
The digital certificate contains
- The certificate serial number
- The expiry date
- The name of the holder
- A copy of their public key
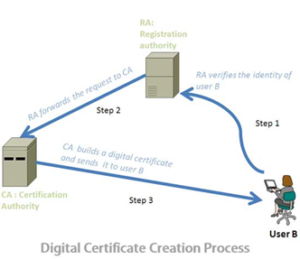
Applying for a Digital Certificate
In order to obtain a digital certificate:
- In order to obtain a digital certificate, for the first time, the applicant sends a request to the registration authority along with proof of their identity e.g. driving licence, business document etc. The registration authority verifies the applicant’s identity and if satisfied then requests a digital certificate from the certificate agency on behalf of the applicant.
- The certificate authority creates the digital certificate using the applicant’s public key and other identity information.
The certificate authority signs the certificate with its own private key in order to ensure the authenticity, integrity and non-repudiation of the digital certificate. Finally, the certificate authority sends back the certificate to the applicant, which can be used to establish secure communication.
Using a Digital Certificate
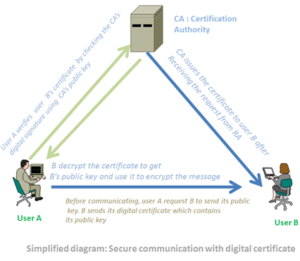
Using the previous process, User B has applied for and being granted a digital certificate. User A wishes to communicate securely with User B:
- User A sends a request for user B’s digital certificate to a certificate repository which is part of the certificate authority.
- When User A receives user B’s certificate it verifies it with the help of web browser by checking the digital signature of the certificate authority using its public key. Then user A uses user B’s public key supplied by the certificate to encrypt the message.
- When user B receives the encrypted message, it uses its own private key to decrypt the message.