Convert the decimal number 164 into the equivalent 8-bit binary number. (1)
Category Archives: Section 1
2014 – Q14
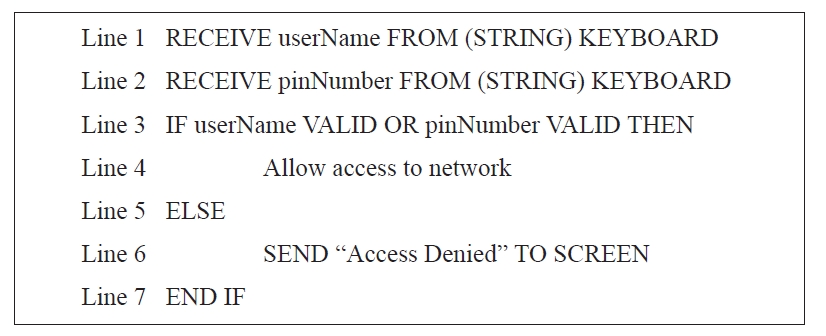
Employees can only access their company network if they enter a correct username and password. A validation program is being developed and will run each time an employee logs on.
An extract of pseudocode from the program is shown below.
An error is noticed when the program is tested.
(a) Identify the line containing a logic error. (1)
(b) State how this error should be corrected. (1)
2014 – Q13
A programmer is developing a stock control program. If a user enters a stock code number from 1 to 900, it will display the number of items in stock.
Give one example of exceptional test data the programmer could use to test the program. (1)
2014 – Q12
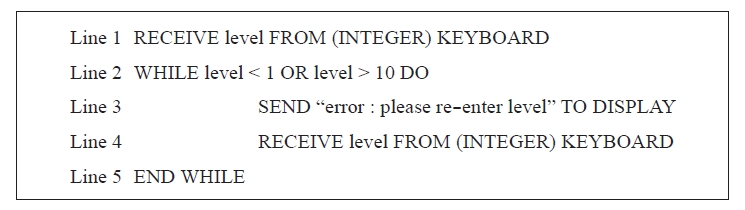
This pseudocode allows a user to enter the level they wish to start playing a game.
Explain what happens if a user enters 12. (2)
2014 – Q11
Hussain is a technician for a new company that has been asked to prepare a presentation on networks. State one difference between peer-to-peer and client/server networks that he could include in his presentation. (2)
2014 – Q10
Businesses and individuals are now making use of cloud services instead of local storage for storing their data.
State one benefit of using cloud based storage instead of local storage. (1)
2014 – Q9
Before going live with a new website, the developer makes sure it matches the original design. Describe one other type of testing that the developer should carry out. (1)
2014 – Q8
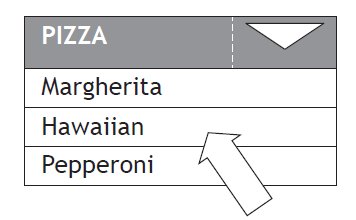
When ordering pizza online, users select their choice from the following drop down menu;
State one advantage of this type of interface. (1)
2014 – Q7
A bank employee has lost a laptop storing customers’ personal details.
Identify one security precaution the bank should have in place to prevent unauthorised access to this information. (1)
2014 – Q6
State one problem with storing data in a flat file database. (1)